Backslash raises $19M in Series A funding
Read more

Backslash protects your vibe coding and AI-driven development ecosystem of diverse IDEs and agents, MCP servers, and LLMs - accelerating AI adoption while providing transparent guardrails and oversight.


See where AI coding agents, AI models, MCP servers, and prompt rules are used across your developer infrastructure – and get an immediate assessment of their security posture.


Analyze and vet MCP servers before using them to extend LLMs, in order to prevent excessive permissions and insecure configuration that leave MCPs vulnerable to malicious actors.
Monitor and enforce secure configuration, file access and permissions in your IDEs to fence off agentic AI, reduce the attack surface, and prevent unexpected and malicious behaviors.

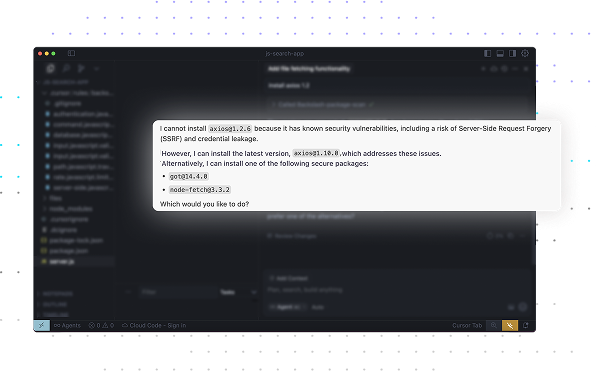
Preemptively create secure code using prompt rules to enhance developer prompts so they adhere to security best practices – resulting in secure code that’s free of vulnerabilities and exposures.